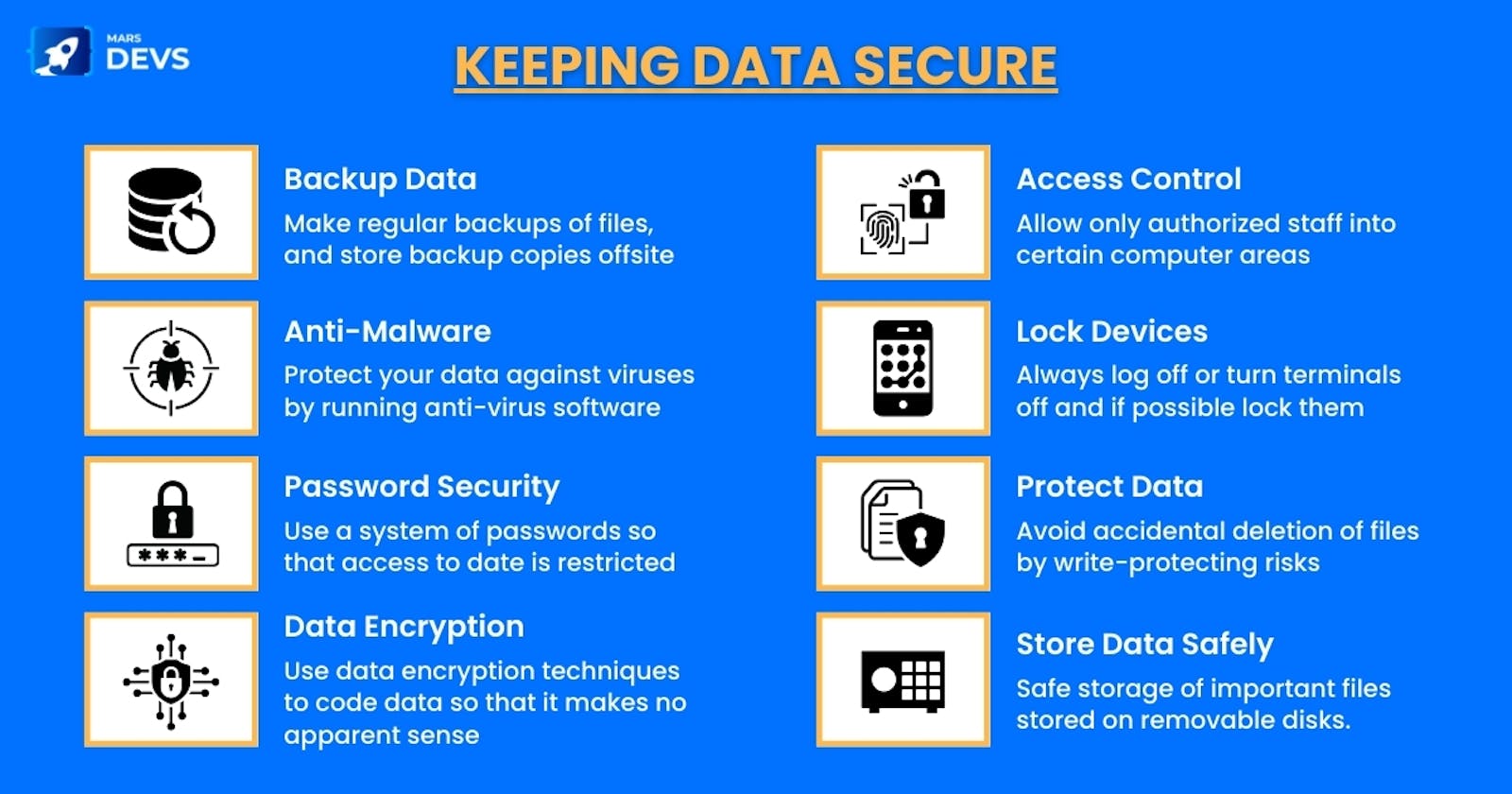
You must keep vigilant and guarantee that your company's data is secure. Limiting data security best practices to the size of the business has never been effective, and it will not be in the future. You should be everywhere, from the server to the endpoint, via the web, at the office, and on your customer's system, blocking any possible loopholes.
Why? Because the risk is real—and increasing. It is no secret that, while hackers frequently target vital corporations, smaller enterprises also appeal to them. The rationale is simple. Small organizations typically have a "not much to steal" approach, employing fewer controls and easy-to-breach data protection techniques.
Hackers collect consumer information with the visible intention of financially exploiting enterprises and customers. In fact, according to Verizon's breach report, “71% of hacks are financially driven.”
And that’s why secure practices are necessary. In this MarsDevs article, we will discuss the five best strategies to make your data more secure! So, let's get started!
Why Data Protection Is a Necessity?
Data protection is a top priority for people, businesses, and organizations of all sizes. With the growing dependence on technology to store and communicate sensitive information, data breaches, and theft have become a big concern.
In 2022, more than 2000 publicly announced data breaches occurred, with hackers accounting for 60% of them. Affected firms and people faced financial and reputational damages, data breaches, and, in some cases, legal liabilities.
You can't safeguard what you don't know exists. As a result, you must accurately understand your data's sensitivity. You should understand how your data is used, who is accessing it, and where it is shared. Collect data from anywhere, including various devices and online services, then categorize it based on sensitivity and accessibility.
Next, develop data security best practices, processes, and policies around them.
5 Essential Strategies For Protecting Your Data
To address these concerns, various methods have been developed to protect data against unauthorized access and modification. Here are the best of 5.
Focus more on encryption:

Encryption is an essential component for securing personal information. It entails turning sensitive information into a coded format unintelligible to anybody without the necessary decryption keys.
Only the authorized user who has the decryption key may decode and access the content. This technology is extensively used to safeguard sensitive data as it’s sent over the internet & to secure data kept on devices like laptops and mobile phones.
Also, encryption models like AES & RSA are employed to shuffle the data, making it extremely challenging for unauthorized intruders. One of the primary advantages of encryption is that it provides high levels of protection, even in the case of a data breach. If encrypted data is stolen or accessed by an unauthorized person, it becomes unintelligible & useless to the attacker.
Furthermore, encryption assists firms in adhering to privacy requirements and standards such as the General Data Protection Regulation (GDPR) and the Payment Card Industry Data Security Standard (PCI DSS).
However, encryption is not a failsafe and must be implemented correctly to be successful. For example, if the encryption key is lost or stolen, the encrypted data becomes unavailable, even to the legitimate owner. Encryption methods can also be cracked, especially if they lack speed with technological advancements and hostile assaults.
Use endpoint security systems:
Your network's endpoints are continuously at risk. To prevent potential data breaches, you must have a robust endpoint security infrastructure. You can begin by applying the following procedures.
Antivirus software: Install anti-virus software on every server and workstation. Conduct frequent scans to ensure your system's health and detect viruses like ransomware.
Antispyware: Spyware is a harmful computer software that typically installs without the user's awareness. Its primary goal is usually to discover insights about user activity and acquire personal information. Anti-spyware and anti-adware software can help you eliminate or restrict them. Install them.
Pop-up blockers: Pop-ups are unwelcome applications that operate on your system for no apparent purpose other than to jeopardize its stability. Install pop-up blockers to be safe.
Firewalls: Because they function as a barrier between your data and fraudsters, most experts consider firewalls one of the most crucial data security best practices. To increase security, you can install internal firewalls.
Implement a risk-based approach to security:
Pay close attention to issues such as the hazards your organization may face and how they may influence employee and customer data. It’s where accurate risk assessment comes into play. Here are a few things risk assessment enables you to do:
Understand what and where your assets are.
Determine your current cybersecurity level.
Manage your security plan correctly.
A risk-based strategy enables you to meet regulatory requirements while protecting your firm from potential leaks and breaches.
Use multi-factor authentication:

Multi-factor authentication (MFA) is regarded as one of the most advanced and effective data protection solutions. MFA works by requiring an additional degree of security before authenticating an account.
It implies that even if the hacker has your password, they must still provide a 2nd/3rd verification element, like a security token, fingerprint, voice recognition, or confirmation on your mobile phone.
Emphasize physical security:
Finally, physical security is vital in data protection since it refers to the procedures for safeguarding physical equipment and facilities that contain sensitive information. It can include securing valuables in secure storage cabinets or vaults, implementing access control systems that employ biometric authentication or key cards, and installing security cameras and alarms in strategic locations.
Portable devices, such as laptops and mobile phones, are equally susceptible to theft or loss but may be safeguarded by encryption, strong passwords, and remote wipe capabilities. However, the main disadvantage of physical security is the human factor.
Human error accounts for 95% of cybersecurity data breaches - even with physical security measures in place, such as misplacing backup media or leaving it unattended. As experts say, “It’s important to keep track of backed-up media locations and ensure they are secure before storing them away.”
In Conclusion
Data security best practices include more than simply the preventative measures listed above. There's more to it, such as performing frequent backups of all data, encrypting it in transit and at rest, mandating secure password procedures & more.
However, you must recognize that cybersecurity does not include eliminating all threats—this isn’t possible. It is also something you should not dismiss. You can substantially minimize risks by using suitable safety procedures.
Need to invest in the best security practices? Get on a free 15-minute call with MarsDevs today!